The Growing Need for Stronger Cybersecurity in U.S. Food and Agriculture
The U.S. Food and Agriculture sector governs our daily activities and quality of life, yet its ubiquity has rendered it invisible in most Americans’ daily discussions and considerations. Like gravity and air, the sector is considered constant. Unfortunately, that false certainty could lead to significant quantifiable risk as the sector becomes continuously under-prioritized and its cyber and physical security is relegated to an afterthought. The U.S. Food and Agriculture sector is often forgotten when discussing critical infrastructure despite accounting for approximately 4 percent of global GDP and consisting of an estimated 2.1 million farms, 935,000 restaurants, and more than 200,000 registered food manufacturing, processing, and storage facilities.
Just because U.S. farms are ignored by the zeitgeist’s perception of bleeding-edge technology does not mean that the sector is not currently undergoing a critical phase of modernization and digital transformation. Worse, ignoring the security concerns surrounding the integration of IoT and internet-enabled systems into Food and Agriculture infrastructure could lead to crippling attacks, devastating shortages, and debilitating inflation.
Digital Transformation on the Horizon
The U.S. Food and Agriculture sector is painstakingly undergoing the digital transformation necessary to meet the modern demands of domestic and international consumers. The recent shift is driven by customer expectations of quality and availability, sustainability, supply chain transparency and traceability, logistics optimization, and other key factors that maximize yield and revenue. Though there is some disparity in the application of the terminology, we are currently experiencing Agriculture 3.0, characterized by the adoption of remote sensors, a reliance on cloud connectivity, a rapid transition towards automation, and the incorporation of real-time variable rate technologies. Data is collected, analyzed, and monitored at each stage of the growth, processing, and transportation cycle. Mission-critical operations are governed by machine learning optimization algorithms that incrementally maximize revenue with each micro-decision.
According to the World Government Summit report, ‘Agriculture 4.0 – The Future of Farming Technology‘, the onset of Agriculture 4.0 is expected around 2030. Success can be gauged according to demographics, scarcity of natural resources, climate change, and food waste. They assert that “Agriculture 4.0 will no longer depend on applying water, fertilizers, and pesticides uniformly across entire fields. Instead, farmers will use the minimum quantities required and target very specific areas.”
The report further states that “farms and agricultural operations will have to be run very differently, primarily due to advancements in technology such as sensors, devices, machines, and information technology. Future agriculture will use sophisticated technologies such as robots, temperature and moisture sensors, aerial images, and GPS technology. These advanced devices and precision agriculture and robotic systems will allow farms to be more profitable, efficient, safe, and environmentally friendly.”
Achieving the technological goals of Agriculture 4.0 is essential because, according to the World Government Summit’s estimation, by 2050, we will need to produce around 70 percent more food at roughly the same or less expected cost and revenue. The metrics above indicate that future needs can only be met through a greater focus on automation and precision agriculture.
As we continue towards Agriculture 4.0, the sector is likely to adopt autonomous systems and artificial intelligence further, incorporate blockchain solutions, and improve systems redundancy and resilience; however, progress is currently limited by technological developments and rural access to highspeed broadband, 5G, and LEO satellite internet. Worse, the U.S. Food and Agriculture sector is susceptible to disruption and increasingly vulnerable to opportunistic and targeted cyber-physical attacks from adversaries ranging from grassroots hacktivists to sophisticated nation-state-sponsored advanced persistent threat (APT) actors.
Disruption Jeopardizes the Food-to-Table Spectrum
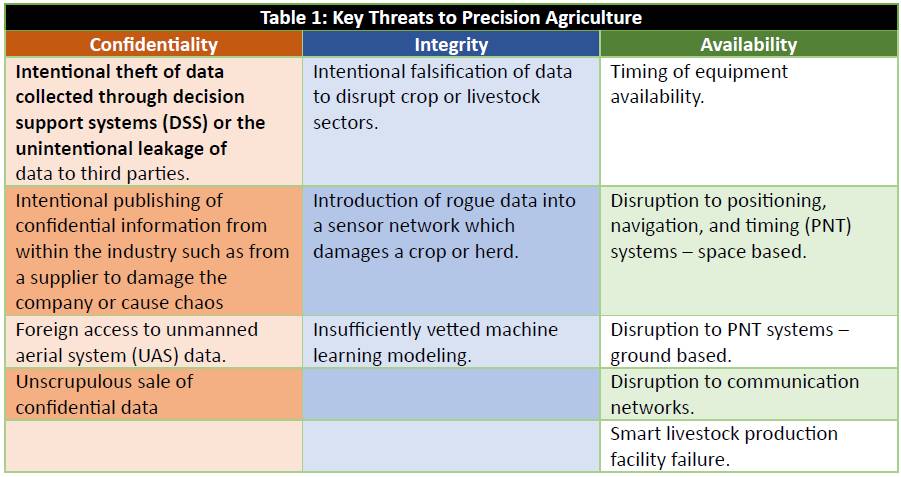
Attacks against agriculture stakeholders of all sizes have annually increased since 2018 in proportion to the digital transformation and modernization of the sector. In Information Security, risk can often be quantified according to scenarios and impacts against mission-critical assets’ confidentiality, availability, and integrity. In 2018 the U.S. Department of Homeland Security released a 25-page report to raise awareness of ‘Threats to Precision Agriculture,’ which designated the top threats to confidentiality, integrity, and availability in the U.S. Food and Agriculture sector respectively as theft of intellectual property and data, targeted disruption and data-driven attacks, and signal loss and data bandwidth limits common in rural communications networks.
Most threats against precision agriculture were shared with other sectors: data theft, stealing resources, reputation loss, destruction of equipment, or gaining an improper financial advantage over a competitor. Common attack vectors were likewise similar, including improper use of USB thumb drives, spear-phishing, and other social engineering. However, precision agriculture is unique in that it is a highly mechanical labor-intensive industry and cyber-physical connections dramatically increase the attack landscape and elevate even common threats to achieve unique and highly significant impacts for minimal effort and resources. Compromise of the confidentiality of agricultural data such as yield data, land prices, herd health, and other factors could lead to significant financial, emotional, or reputational harm for farmers, manufacturers, and other agricultural stakeholders. Meanwhile, as agriculture embraces “smart systems,” the potential increases for data collection and exploitation and for the compromise of automated equipment, mission-critical legacy systems, and IT-OT systems.
Finally, availability issues range from cyber disruption attacks to incidents that impact the timely response to national disasters and events. Equipment loss in the food and agriculture sector is heavily time dependent and loss of availability for even a few critical hours could cascade into devastating impacts in the following days or months. Key threats to precision agriculture are detailed in Table 1.
Similarly, in 2020, the UK National Cyber Security Centre (NCSC) created a 14-page guide, ‘Cyber Security for Farmers‘, to help educate sole traders, small to medium-sized operators, and large-scale commercial farms on cybersecurity and cyber-hygiene fundamentals. From July 2021 to March 2022, the FBI noted ransomware attacks against a multi-state grain company, a feed milling company, six grain cooperatives, and a business management software company that serviced agriculture cooperatives. As a result, it issued a bulletin warning that such attacks could “impact the planting season by disrupting the supply of seeds and fertilizer.”
Ransomware and cyberattacks against organizations across the farm-to-table spectrum of the Food and Agriculture sector were already common, but the increase in propensity during key seasons indicated a driven intent rather than opportunistic exploitation. Adversaries likely correlated their attacks with critical seasons to compel victims to pay the ransom under the risk of a diminishing crop yield. The attacks on specifically grain facilities were also notable as foreign grain markets were disrupted during early 2022 by the conflict in Ukraine and because grain production governs the entire food chain from bread products to livestock feed. Each compromise traced to a deficit in cybersecurity and cyber-hygiene best practices.
Concluding Recommendations
As Agriculture 3.0 and, eventually, Agriculture 4.0 will depend on modern systems comparable to those deployed across the other 15 U.S. critical infrastructure sectors, it behooves owners and operators to improve their fundamental cybersecurity and cyber-hygiene according to the following recommendations:
Practice Fundamental Cybersecurity Best Practices
- Install updates and patch operating systems, software, and firmware upon release.
- Install and regularly update anti-virus and anti-malware software on all hosts.
- Use strong passwords and regularly change passwords to network systems and accounts, implementing the shortest acceptable timeframe for password changes. Avoid reusing passwords for multiple accounts and use strong passphrases where possible.
- Disable hyperlinks in received emails, and consider adding an email banner to messages from outside your organization.
- Focus on cyber security awareness and training. Regularly provide users with training on information security principles and techniques, as well as overall emerging cybersecurity risks and vulnerabilities (i.e., ransomware and phishing scams).
- Reduce attack incidence by implementing email and web browser protections. Allow only authorized web browsers (with various scripts disabled) to access precision agriculture systems and networks.
- Limit and control network ports, protocols, and services. Unsecured ports, protocols, and services may allow a remote attacker to gain access to critical systems. Limiting these communications pathways to only authenticated and authorized systems mitigates several threat vectors. A critical control is only allowing remote desktop access through virtual private networks (VPNs) or other encrypted pipelines.
- Inventory and control hardware assets. Encourage network owners to inventory all devices to establish an authorized device profile and detect unauthorized devices. This control is often not implemented at the farm level but is essential at the precision agriculture vendor level.
- Inventory and control software assets. Like the inventory of hardware assets, this control calls for Organizations should inventory their various software packages the same way they inventory hardware assets. This control helps track necessary security updates and can also be used to identify authorized and unauthorized software running on precision agriculture systems.
- Establish account monitoring, controls, and access levels for authorized users to mitigate insider threats and lateral compromise.
- Separate Operational Technologies like fertilizer distribution machinery and tractors from traditional business networks to mitigate risk to the physical machinery. This separation can be facilitated by virtual local area networks (VLANs), firewalls, and cyber-defined demilitarized zones.
Quantify and Manage Risk
- Understanding Data Ownership: A critical area of concern for precision agriculture users is understanding who owns what data. Contracts with precision agriculture vendors may change data ownership and impact the privacy of data to which farmers believe they have exclusive rights. Understanding these contracts is critical for securing farm data.
- Identify mission-critical assets and functions and deploy security protections according to their exposure or loss if compromised.
- Developing and practicing an Incident Response and Management plan will allow for more rapid recovery from major threats and incidents.
- Develop an operations plan in case systems are rendered unavailable. Regularly practice the plan to ensure its actionability.
- Implement system redundancy where possible and create a recovery plan that includes maintaining and retaining multiple copies of sensitive or proprietary data and servers in a physically separate, segmented, secure location (i.e., hard drive, storage device, the cloud) [4].
- Redundant physical controls can act as a defense-in-depth strategy that augment cyber security controls. Farmers and precision agriculture manufacturers may consider adding physical security controls restricting access to key technology areas.
- Regularly back up data, air gap, and password-protect backup copies offline. Ensure copies of critical data are not accessible for modification or deletion from the system where the data resides.
Adopt Zero Trust Frameworks
- Implement network segmentation.
- Use multi-factor authentication where possible.
- Disable unused remote access/RDP ports and monitor remote access/RDP logs.
- Require administrator credentials to install software.
- Audit user accounts with administrative or elevated privileges and configure access controls with least privilege in mind.
- Only use secure networks and avoid using public Wi-Fi networks. Consider installing and using a virtual private network (VPN).






